Continuous Vulnerability Management
Nodeware exists to give MSPs a way to start the journey into vulnerability management, or find an alternative to traditional solutions, saving them time and money. Experience continuous vulnerability management with swift deployment, real-time protection, and faster identification and remediation.
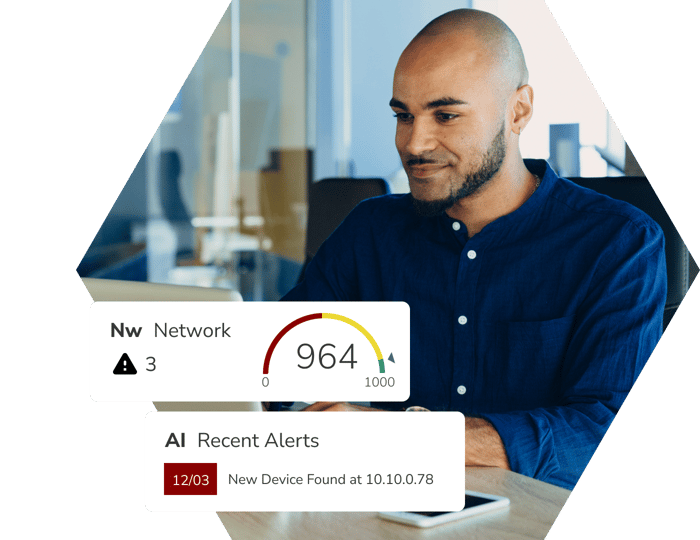

We Made Cybersecurity Easier
For a secure, efficient cybersecurity experience, choose Nodeware. Continuous vulnerability management ensures 24/7 up-to-date vulnerability data within the multi-tenant dashboard. Experience modern innovation with features designed to easily identify, manage, and remediate and patch vulnerabilities exponentially quicker than traditional solutions.
Add a Critical Layer to Your Cybersecurity Offerings
Nodeware simplifies every step of vulnerability management, from deployment to remediation. Discover how our solution transforms how you proactively identify and address security gaps.

Deploy
30 minutes — that’s all it takes to get up and running with Nodeware. Our solution is designed for versatility, offering deployment options with virtual agents or sensors. Integrate across various platforms without the need for additional hardware or on-site visits.

Manage
Managing multiple clients becomes a breeze with Nodeware's multi-tenant dashboard. It provides a comprehensive asset inventory, vulnerability risk ranking, remediation guidance, and patch management all in one place.

Remediate
Patch management and built-in guidance reduce the resources needed for effective vulnerability management. Nodeware ensures quick, efficient handling of vulnerabilities, all while saving you time and money.
Trusted By Leading Industry Partners
Nodeware’s strategic alliances with leading industry partners offer you enhanced capabilities designed to complement and align with your workflow and processes.











Elevate Your Security Standards
Say hello to the future of vulnerability management. Nodeware offers continuous, non-disruptive scanning with data that is real-time. We provide comprehensive vulnerability information, as well as a complete asset inventory. Coupled with real-time alerts and robust reporting, Nodeware is more than just a vulnerability management solution; it's a strategic partner that empowers you to reduce your clients’ risk and streamline your operations.

“Nodeware has transformed our vulnerability scanning with seamless deployment and intuitive agent-based scans. The centralized dashboard provides a clear view of vulnerabilities for efficient remediation, and continuous scanning keeps us updated on the latest threats. We highly recommend Nodeware for its user-friendly interface, robust features, and exceptional support.”
Jake Geier
Information Security Consultant, Pivotalogic

“Nodeware stood out from the start with its intuitive reporting, well-designed dashboard, and ease of use for our engineers. Since implementing it, we’ve seen significant improvements in our clients' security posture. With continuous enhancements, the platform stays ahead of the curve, and its support team is exceptional—attentive, proactive, and always ready to help. We highly recommend Nodeware to our peers in the MSP industry as a versatile solution, especially for clients with regulatory compliance needs.”
John Iacono
Partner, Chief Information Officer, Fairdinkum

“Nodeware has become an essential tool in our cybersecurity stack. It does an outstanding job of identifying network assets and their vulnerabilities in our customers’ networks and provides concise reporting that gives your technical support team the details to mitigate the issues. I can assure you that Nodeware will give you the advantage in protecting your customers’ networks and data.”
Rick Raesz
President and CEO, RCOM Computer Services

“We chose Nodeware over other vulnerability management scanners because we were having problems running our previous vulnerability management tool during business hours. Nodeware is perfect because I can run it quietly in the background without disruption all day and night and it provides clear and concise reporting that we can easily share with our clients’ executive management team.”
Nick McCourt
Lead vCISO, Integris



