Nodeware Agents and Sensors running authenticated scans can now detect Log4j vulnerable applications as part of regular vulnerability scans. You can read the full press release here.
This additional scanning capability is delivered as an over-the-air update and does not require user interaction to enable. Updates are downloaded on a rolling basis to Nodeware Agents and Sensors, the Log4j versions are below, as well as instructions on how to confirm what version you’re running.
-
Windows Agents version 3.0.2.0 and later
-
Windows Sensors version 2.2.0.0 and later
-
Hyper-V Virtual Sensors version 3.3.9 and later*
-
VMware Virtual Sensors version 3.3.9 and later*
-
Hardware Sensors version 3.3.9 and later*
-
macOS Agents version 1.3.0 and later
-
Linux Agents version 1.0.0 and later
*Authenticated scanning required. For instructions, see this knowledge base article.
Checking Nodeware Sensor Version
Sensor versions can be found under the Sensors view, in the upper right corner of the Sensor tile. If the version is not the latest available, there will be a warning icon and message displayed. Updates are downloaded on a rolling basis, but if you see the warning for longer than 2 hours, create a support ticket at support.nodeware.com for assistance.
Checking Nodeware Agent Version
After selecting the Nodeware Agent in the Asset view, hover over the Agent tile in the top section and a pop up will display the current version. If you encounter an out of date Agent that is online, you can rerun the installation package found in the Downloads section over top the existing installation to force an update immediately, or wait for the over-the-air update to be received. If you have issues updating an agent, create a support ticket at support.nodeware.com.
Original Post:
The whole world has been posting updates and papers on how to deal with the Log4 Vulnerability CVE-2021-44228 and CVE-2021-45046 and we at IGI CyberLabs have been working to deliver you a complete detection solution. With our newly created Windows User Interface, the process is as easy as 1. [Right Click ]— 2. [Select “Run as Administrator”] — 3. [Select "Scan"].
Download it here: https://downloads.nodeware.com/log4j_scan.exe
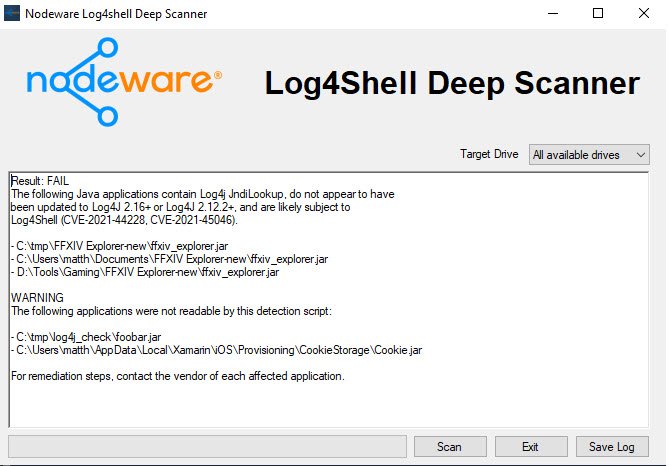
Also, for Mac and Linux environments, we have developed a Log4j discovery script which can be found below:
/bin/bash -c "$(curl -fsSL https://downloads.nodeware.com/log4j_scan.sh)"
Copy Command
To run, simply copy the above script and paste it in a terminal window on your Mac or Linux machine.
If further support is needed, please contact support via the dashboard or support@nodeware.com.
If you believe you are facing a cyber incident or are concerned you have been targeted by cyber criminals, you can contact our sister company IGI Cybersecurity for help with incident response, penetration testing, and more.
More from the blog
View All PostsHow Log4j is Exploited and Tips to Stay Protected
Nodeware Introduces Deep Scanning to Boost Cybersecurity
EDR vs Vulnerability Management Scanning: Understanding the Difference and Enhancing Your Security
Subscribe to email updates
Stay up-to-date on what's happening at this blog and get additional content about the benefits of subscribing.

